Watch out for hacking from unauthorized routers and wireless clients that are attached to your network and running in ad-hoc mode. By using NetStumbler or your client manager software, you can test for access points (APs) and ad-hoc devices that don't belong on your network. You can use the network monitoring features in a WLAN analyzer, such as OmniPeek and CommView for WiFi.
Look for the following rogue AP characteristics:
• Odd SSIDs, including the popular default ones such as linksys and free wifi.
• Odd AP system names - that is, the name of the AP if your hardware supports this feature. Not to be confused with the SSID.
• MAC addresses that don't belong on your network. Look at the first three bytes of the MAC address, which specify the vendor name. You can perform a MAC-address vendor lookup to find information on APs you're unsure of.
• Weak radio signals, which can indicate that an AP has been hidden away or is adjacent to or even outside of your building.
• Communications across a different radio channel(s) than what your network communicates on.
• Degradation in network throughput for any WLAN client.
NetStumbler has found two potentially unauthorized APs. The ones that stand out are the two with SSIDs of BI and LarsWorld.
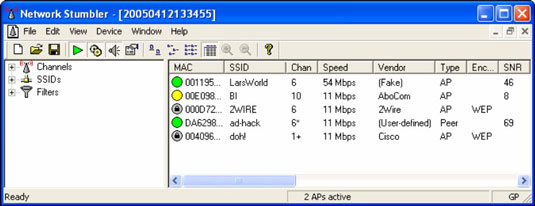
NetStumbler does have one limitation: It won't find APs that have probe response packets disabled. Commercial wireless network analyzers such as CommView for WiFi as well as the open source Kismet look not only for probe responses from APs like NetStumbler does, but also for other 802.11 management packets, such as association responses and beacons. This allows Kismet to detect the presence of hidden WLANs.
If the UNIX platform is not your cup of tea, and you're still looking for a quick and dirty way to root out hidden APs, you can create a client-to-AP reconnection scenario that forces the broadcasting of SSIDs using de-authentication packets.
The safest way to root out hidden APs is to simply search for 802.11 management packets. You can configure OmniPeek to search for 802.11 management packets to root out hidden APs by enabling a capture filter on 802.11 management packets.
You can use CommView for WiFi to spot an odd network host; for instance, the Hon Hai and Netgear systems if you know you only use Cisco and Netopia hardware on your network.
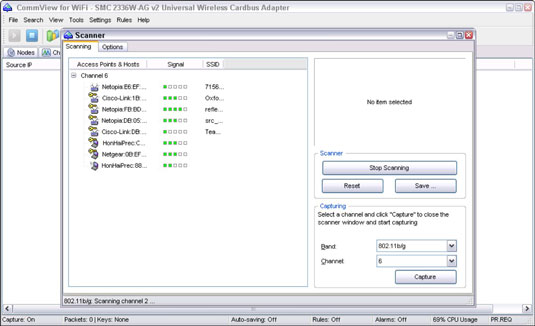
My test network for this example is small compared to what you might see, but you get the idea of how an odd system can stand out.
WLANs set up in ad-hoc mode allow wireless clients to communicate directly with one another without having to pass through an AP. These types of WLANs operate outside the normal wireless security controls and can cause serious security issues beyond the normal 802.11 vulnerabilities.
You can use just about any WLAN analyzer to find unauthorized ad-hoc devices. If you come across several ad-hoc systems, such as those devices listed as STA in CommView for WiFi's Type column, this could be a good indication that people are running unprotected wireless systems or have ad-hoc wireless enabled. These systems are often printers or seemingly benign network systems, but can be workstations and mobile devices.
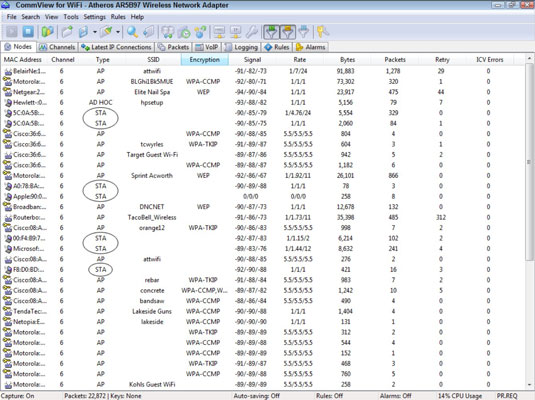
You can also use the handheld Digital Hotspotter to search for ad-hoc–enabled systems or even a wireless intrusion prevention system to search for beacon packets in which the ESS field is not equal to 1.
Walk around your building or campus to perform this test to see what you can find. Physically look for devices that don't belong and keep in mind that a well-placed AP or WLAN client that's turned off won't show up in your network analysis tools.
Keep in mind that you might be picking up signals from nearby offices or homes. Therefore, if you find something, don't immediately assume it's a rogue device. The strength of the signal you detect is a good indication.
Devices outside your office should have a weaker signal than those inside. Using a WLAN analyzer in this way helps narrow the location and prevent false alarms in case you detect legitimate neighboring wireless devices.
A good way to determine whether an AP you discover is attached to your wired network is to perform reverse ARPs to map IP addresses to MAC addresses. You can do this at a command prompt by using the arp -a command and simply comparing IP addresses with the corresponding MAC address to see whether you have a match.
Also, keep in mind that WLANs authenticate the wireless devices, not the users. Criminal hackers can use this to their advantage by gaining access to a wireless client via remote-access software, such as telnet or SSH, or by exploiting a known application or OS vulnerability. After they do that, they potentially have full access to your network.
The only way to detect rogue APs and wireless hosts on your network is to monitor your WLAN proactively, looking for indicators that wireless clients or rogue APs might exist. A WIPS is perfect for such monitoring. But if rogue APs or clients don't show up, that doesn't mean you're off the hook. You might need to break out the wireless network analyzer, wireless IPS, or other network management application.
Depending on your AP, a couple of configuration changes might keep hackers from carrying out these hacks against you:
• If possible, increase your wireless beacon broadcast interval to the maximum setting, which is around 65,535 milliseconds. This can help hide the AP from hackers who are wardriving or walking by your building quickly. Be sure to test this first, though, because it might create other unintended consequences, such as legitimate wireless clients not being able to connect to your network.
• Disable probe responses to prevent your AP from responding to such requests.
Use personal firewall software, such as Windows Firewall, on all wireless hosts to prevent unauthorized remote access into your hosts, and subsequently, your network.
About the Book Author
Kevin Beaver is an independent information security consultant with more than three decades of experience. Kevin specializes in performing vulnerability and penetration testing and security consulting work for Fortune 1000 corporations, product vendors, independent software developers, universities, and government organizations. He has appeared on CNN and been quoted in The Wall Street Journal.
Stop hackers before they hack you!
In order to outsmart a would-be hacker, you need to get into the hacker's mindset. And with this book, thinking like a bad guy has never been easier. In Hacking For Dummies, expert author Kevin Beaver shares his knowledge on penetration testing, vulnerability assessments, security best practices, and every aspect of ethical hacking that is essential in order to stop a hacker in their tracks.
Whether you're worried about your laptop, smartphone, or desktop computer being compromised, this no-nonsense book helps you learn how to recognize the vulnerabilities in your systems so you can safeguard them more diligently-with confidence and ease.
• Get up to speed on Windows 10 hacks
• Learn about the latest mobile computing hacks
• Get free testing tools
• Find out about new system updates and improvements
There's no such thing as being too safe-and this resourceful guide helps ensure you're protected.
More Network Security Articles:
• Are You Meeting ISO 27000 Standards for Information Security Management?
• Cyber Security Tips for Small and Medium Business (SMB)
• The Role of Security Penetration Testers
• Difference Between Rule and Role Based Access Control
• Network Security Across the Enterprise
• What is Network AAA (Authentication, Authorization, and Accounting)?
• How Snort's Stealth TCP Port Scanning Works
• What is Penetration Testing?
• Secure, Network Compliant BYOD (Bring Your Own Device) Solutions
• Remote Access Authentication Protocols



