You should scan your Linux-based systems to avoid hacks and gather information from both outside (if the system is a publicly-accessible host) and inside your network. That way, you can see what the bad guys see from both directions.
System scanning
Linux services - called daemons - are the programs that run on a system and serve up various services and applications for users.
• Internet services, such as the Apache web server (httpd), telnet (telnetd), and FTP (ftpd), often give away too much information about the system, including software versions, internal IP addresses, and usernames. This information can allow hackers to exploit a known weakness in the system.
• TCP and UDP small services, such as echo, daytime, and chargen, are often enabled by default and don't need to be.
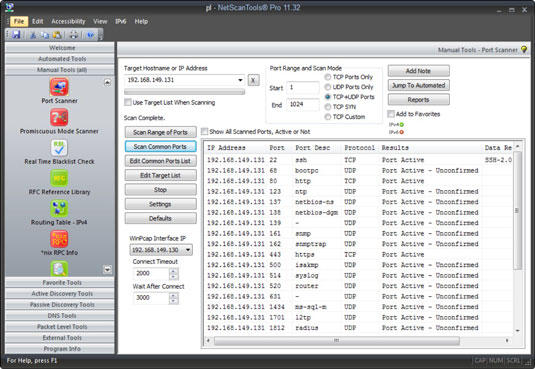
The vulnerabilities inherent in your Linux systems depend on what services are running. You can perform basic port scans to glean information about what's running.
The NetScanTools Pro results show many potentially vulnerable services on this Linux system, including the confirmed services of SSH, HTTP, and HTTPS.
In addition to NetScanTools Pro, you can run another scanner, such as LanGuard, against the system to try to gather more information, including the following:
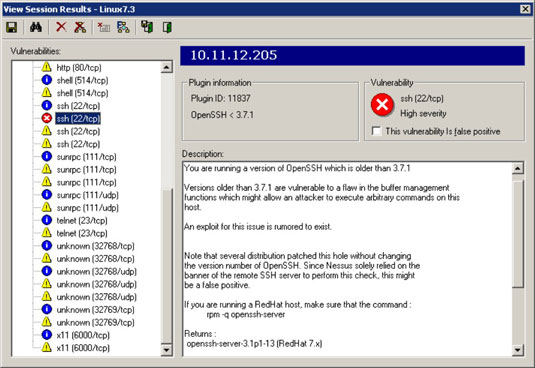
• A vulnerable version of OpenSSH (the open source version of SSH) returned by Nessus
• The finger service information returned by LanGuard Network Security Scanner
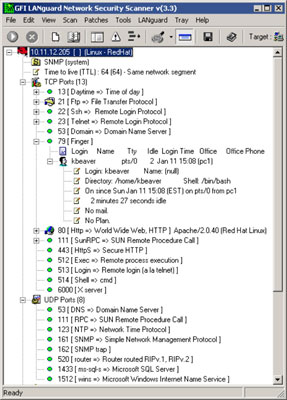
LanGuard also determined that the server is running rlogin and rexec, the Berkeley Software Distribution (BSD) r-services. This information can be handy when you come across unfamiliar open ports.
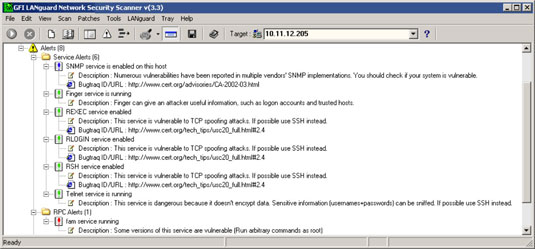
Notice that LanGuard points out specific vulnerabilities associated with some of these services, along with a recommendation to use SSH as an alternative.
TIP You can go a step further and find out the exact distribution and kernel version by running an OS fingerprint scan with the Nmap command nmap -sV -O.
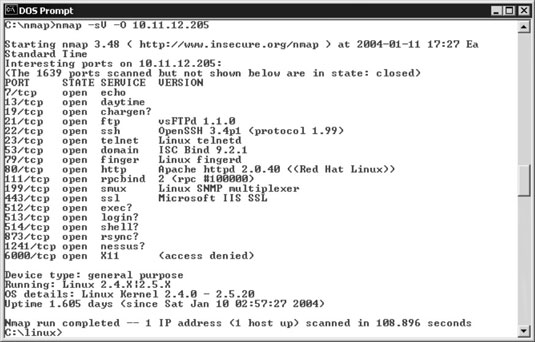
The Windows-based NetScanTools Pro also has the capability to determine the version of Linux that's running.
Countermeasures against system scanning
Although you can't completely prevent system scanning, you can still implement the following countermeasures to keep the bad guys from gleaning too much information about your systems:
• Protect the systems with either
o A firewall, such as iptables that's built into the OS
o A host-based intrusion-prevention application, such as PortSentry and SNARE
• Disable the services you don't need, including RPC, HTTP, FTP, telnet, and the small UDP and TCP services - anything for which you don't have a true business need. This keeps the services from showing up in a port scan, which gives an attacker less information - and presumably less incentive - to break in to your system.
• Make sure the latest software and patches are loaded to reduce the chance of exploitation if an attacker determines what services you're running.
About the Book Author
Kevin Beaver is an independent information security consultant with more than three decades of experience. Kevin specializes in performing vulnerability and penetration testing and security consulting work for Fortune 1000 corporations, product vendors, independent software developers, universities, and government organizations. He has appeared on CNN and been quoted in The Wall Street Journal.
Stop hackers before they hack you!
In order to outsmart a would-be hacker, you need to get into the hacker's mindset. And with this book, thinking like a bad guy has never been easier. In Hacking For Dummies, expert author Kevin Beaver shares his knowledge on penetration testing, vulnerability assessments, security best practices, and every aspect of ethical hacking that is essential in order to stop a hacker in their tracks.
Whether you're worried about your laptop, smartphone, or desktop computer being compromised, this no-nonsense book helps you learn how to recognize the vulnerabilities in your systems so you can safeguard them more diligently-with confidence and ease.
• Get up to speed on Windows 10 hacks
• Learn about the latest mobile computing hacks
• Get free testing tools
• Find out about new system updates and improvements
There's no such thing as being too safe-and this resourceful guide helps ensure you're protected.



