Penetration testing is always evolving. More complex cyberattacks require more sophisticated pen tester. Here are ten tips to help you refine your pen testing skills as you continue in your career or education.
Continue your education to improve your pen testing skills
Keep learning. Study often and do not limit the scope of your studies. You can get by in your career by learning the basics, getting the tools, and running them. However, you need to learn the finer details of information technology systems, networks, and services and how they are secured or threatened.
The ways you can continue your education are unlimited. However, if on a budget (or have resources to access resources within a budget), here are a few ways you can help yourself:
• Use your library. To access the Internet, books, publications, magazines, and other materials, use your public library system. Some libraries even hold IT classes, and in some cases, even security classes.
• Use the Internet. You can find many sites to help with pen testing, learning about IT, security, and many other topics. You can gain access to tools and sites that allow you to learn how to conduct penetration testing, and learn operating systems and other valuable programs.
• Build a test PC. If you can gain access to a PC or laptop that you can turn into a test system, acquire it and use it. There are many companies likely have an older system laying around unused that you can turn into a pen test toolkit.
• Use virtualization. Similar to the extra PC or laptop, you can set up virtualization software that allows you access to even more systems so you can build a small virtual network within a computer and you can conduct pen testing on multiple systems from one system. The image below shows an example of a tool running within a virtualized system.
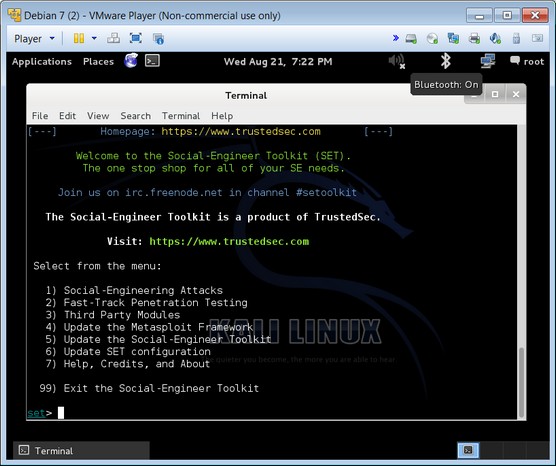
Using Kali and VMware virtualization
• Use freeware. Many demo tools give you full access for a period of time, or at least with limited functionality, that you can use to learn with.
Build your penetration testing toolkit
Carpenters and other trades rely on their tools to be able to do their jobs. Auto mechanics, welders, and others who use tools to conduct their work can't do great work without tools that are maintained and preserved. The same is true of IT professionals, especially those who function in the security realm as pen testers.
No matter what, consider your tools as the most important thing you can maintain. Keep the following in mind as you build your toolkit:
• Keeping your toolkit current is one of the hardest things to do as a pen tester. You will find some tools (sometimes older tools) are more helpful to getting the results you need. Some tools are scripts that are created and maintained by each individual pen tester.
• Some tools are expensive, and you need to license for them. You also need to keep them updated. For example, any tools, software, programs, applications, and systems you use need to be patched, virus scanned, updated, and kept up to date.
• All software must be updated. Any software that requires signature files, digital certificates, block ciphers, and any other form of additional software needs to be updated and maintained.
• Technology changes over time. There will be updates to the systems you use, and there will be different systems in different organizations - all this means you need to keep your toolkit current with new additions as you find you need them.
• Make sure your computer is updated and safe. Make sure you keep the system you run all this on current as well. Nothing is worse than the embarrassment of getting your own system hacked as a pen tester. Keep your own stuff pristine, secure, and tested.
Think outside the box to be a better pen tester
Never get comfortable with the same vectors, tools, patterns, and attacks. Always consider another option. The plan B. You have to constantly think outside the box to stay ahead of those who commit crimes.
TIP
Think of hackers and attacks like running water. It will find a way. You too need to think like
running water and consider, anticipate, and get ahead of different types of attacks and vectors
for attacks by developing this dynamic mindset.
Below is an example of a planned penetration test where the pen tester wanted to enter the network via the wireless access point. In a situation where one pen tester was working with an organization that agreed to trying another path if possible, he found another way through the Internet connection (plan B) to access the network externally. He could also have accessed the network from picking up a signal from the parking lot.
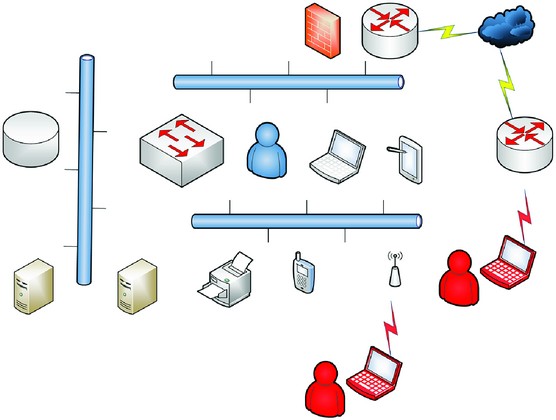
Using a Plan B alternative
Think like a hacker to be a better pen tester
You need to know what hackers do. As an ethical person, it's not easy to think like a criminal. This is where the great pen testers excel. You have to think beyond what a good guy would do… what someone who has ethics would do.
Ways to help you develop this is by reading. You can read attacks that took place in the past to learn about those who conducted them. One of the oldest hackers of the past is Kevin Mitnick who conducted hacks back in the'90s when he was arrested in 1995. Learning about Kevin and how he turned into a grey hat hacker over time helps to get inside the mind of those who conduct crimes and their motives.
Get involved to improve as a pen tester
Whether it be conferences, online communities, or social outlets online or in person, spend some time networking with others in your field.
Two conferences where you can continue your education, learn specifics of pen testing from experts in the field, meet book authors, and get access to current trends and classes about current products is Defcon and Blackhat. Normally both are held in the United States, but over the years the conference has grown and expanded to other countries as well.
Both of these sites will have options to sign up for a conference, but have other options as well to view older media, papers and research conducted over the years. It is also a great way to meet other experts in your field as you continue to grow within it.
There are professional organizations that cater to pen testers, schools that form groups of likeminded individuals, governance committees, and other types of groups that allow those who conduct ethical hacking to join together and share ideas. There are government agencies that you can join to work more closely with LEO and military or other government agencies to share ideas and information.
TIP
Regardless of who you join up with, a community-based approach to sharing ideas has led to
some of the larger crowdsharing/crowdsourcing and other group-like successes there are today.
Pair up and work on some projects together to share ideas and learn more about pen testing.
Use a lab for penetration testing
If you buy and build one, rent space, or lease system time from others, use online resources available to you for testing or through the use of virtual machines in a lab you build - hands-on time is crucial to your success. You need to be able to run the tools, hacks, tests, and see what is possible. It's one of the best ways to learn how to become an elite pen tester.
Because there are many challenges to do this, you can still learn ways to get hands-on training:
• Online test sites: Online test sites let you experiment with your penetration-testing skills.
• A test machine: You can also set up on one computer in your home a virtual system of other machines (a virtual network) and test the systems on your base machine.
The image below lays out a nice lab strategy you can use to start to develop a pen testing practice lab at work or at home.
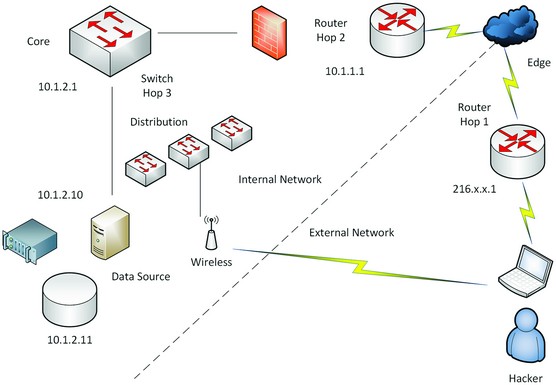
Creating a viable lab.
• Server infrastructure: You can either set up a server physically on your mock network or a virtual one. Either way, make sure that you have allocated resources so that you can configure targets such as a database (can be large in size), as well as multiple network connections for redundancy (cluster) or other advanced setups.
• Network infrastructure: From the cabling to the wireless systems -the routers, switches, access points, firewalls, and everything in between - you can configure all the network components to interconnect the devices you want to set up as resources on your mock network.
• Pen test system: The point of origin, which can be the laptop that you use as an ethical hacker to conduct the penetration testing.
As you learn more and more, you can add systems and infrastructure to further build out the lab so you can conduct more tests.
Stay informed on penetration testing
Just like any other role, skill, or function, the more you know the better off you will be. Up-to-date threat information can help you learn about the myriad of attacks and patterns coming out daily. This information deepens your knowledge of what you need to be aware of as a pen tester protecting against them.
TIP
You should also stay abreast of things going on in the pen test community. One great way to do
this is by meeting up with others pen testers to swap information.
Stay ahead of new technologies to be a better pen tester
Technology is always changing. Remember when virtualization became important? Cloud? Wireless? Mobile? As each of these technologies emerged (and in some instances converged), it was important to stay on top of them because the minute they came to market, there seemed to be a ton of attacks that came right along with them.
When wireless hit the market, for example, there were drive-by scanners hanging out of cars - hackers were cracking into systems in companies from the parking lot. You must know about new technologies, learning about them, and anticipating how black hat hackers might use them.
There are countless resources available to learn of new technology. For example, if you know your primary targets are going to be Cisco, Citrix, Microsoft, VMWare, Linux (select a distribution), and EMC Storage, you may want to add yourself to those vendors' websites and their mailing lists to stay ahead of updates, new patches, version updates, and so on.
If you have a contract with any of these vendors, they should be sending you information; however, anyone can contact these vendors and be added to their mailing lists so you can learn more about them. For example, if you were a large Cisco networking customer, you can gain access to RSS feeds, field notices, security advisories, bug alerts, software updates, and so much more.
Build your reputation as a pen tester
Building your reputation is easy. For someone (anyone) to let you into these protected networks where all their data sits, they absolutely must trust you. Trust. It's the critical piece of the proverbial pie of your career in pen testing. Identify as someone who can't be trusted, and it's likely you will never work for a company that needs your assistance in thwarting crime again.
This means you cannot be a criminal! You need to make sure you act professionally and ethically. Build your network of peers and people who can vouch for you and continue to act in a way that is honorable and as a consummate professional.
Learn about physical security
All the technical knowledge, skill, tools, and experience in the world can't save you and a company from a social engineering attack. Nothing can thwart technical security faster than social engineering.
Card swipes, magnetic door locks, bio-sensor reading, cameras, physical security guards, wall hopping, and all of the other things that fall outside of the computer network where data is kept can't stop someone from breaking and entering.
Always consider physical security challenges as a pen tester and augment your technical vulnerability analysis and scans with checking how physical security and defense in depth stacks up.
Ultimately, any efforts you can take to learn will help to make you a better pen tester. Learning is key.
About the Book Author
Robert Shimonski is an ethical hacker and a professional IT leader who has led numerous efforts to architect, design, strategize and implement enterprise solutions that must remain secure. Rob has been involved in security and technology operations for over 25 years and has written his books from the trenches of experience.
More Network Security Articles:
• Intrusion Detection System (IDS) and Intrusion Prevention System (IPS)
• Firewall Internet Security - The Basics of a Firewall
• Methods to Combat Distributed Denial of Service (DDoS) Attacks
• Man in the Middle Attack
• Remote Access Authentication Protocols
• What is a SQL Injection Attack?
• Public Key Infrastructure
• What's the Difference Between Sniffing, Snooping, and Spoofing?
• Designing Physical Network Security
• How to Become a Professional Ethical Hacker


