After you complete the preparation work, you're ready to do a pen test! Here you walk through the process of the penetration test and then look at the results of the assessment as well as methods of prevention.
WARNING
Always be absolutely careful when you're working on a live network
in production. Even better is to use a lab to learn how to conduct a pen test prior to doing
it on a live network. In the spirit of measure twice and cut once, please make sure you are careful.
For this pen test you will be starting at the network edge externally and attempting to make your way inside via any weaknesses found outside the network perimeter. Here, you review each portion of the pen test so you can see a building block approach that you can adapt to future projects. Successful attacks might differ regarding your intentions and methods, but each successful attack essentially contain these actions, which happen in this order and which you'll mimic during a pen test:
1. Infiltration.
Just gaining access is fairly easy and straightforward where those with access to hacking tools such as script kiddies can basically run attacks all day probing your defenses, looking for ways in and if they are lucky enough… get in.
This means that an attacker had to be connected to the technology that they want to exploit. You want to make sure that you test and scan for vulnerabilities that disallow anyone who is unauthorized to connect to a network they don't belong to. This should at least minimize the amount of attacks just by who is able to sneak past and connect with this first level of security. Defense in depth should start to thwart an attack. Make sure that you disallow login access from devices that can be probed in this fashion. An access control list (ACL) can be configured on the device to tell it to only allow access from trusted IPs.
2. Penetration.
Once access is gained, another level of access can be gained. This hop by hop strategy is used by more experienced hackers who can gain access (via malware as an example in the form of a Trojan horse) and then launch another attack or move to another segment of your network looking for more access or data.
By attempting to spoof, connect, gain access, raise, and escalate privilege, assume the roles of other systems, and get in the middle of conversations the attacker is able to potentially do a vast amount of damage. An attacker could have run an APT and conducted eavesdropping that may have provided them more passwords or data. By running tools such as Burp Suite, Nessus, and Wireshark you can assess these vectors and ensure that access is limited in this area.
3. Exploit.
At this stage, the hacker builds upon the previous level where access and access to data is actually achieved or granted and something of value can be garnished from the attack.
Exploit is when the attacker has conducted the attack to gain and assume control; however, the next step would be to actually do the exploit. Steal data, take credentials, lay in wait for an APT, and do what they do. You can conduct similar attacks to see whether tools can flag these types of attacks taking place and how the security team can better monitor (and respond) to them.
4. Conduct an advanced persistent threat.
The final level of this multilevel attack is the APT. To gain access, maintain it, have the ability to move around, and eventually gain access to valuable data while being undetected is the most valuable attack of them all.
5. Exfiltration.
If they're able to do the previous steps and vanish without a trace, they have been highly successful in their attack.
TIP
You want to do the same as a pen tester and see whether you can set up ways
to identify whether someone has been in the system without your knowledge. In the scenario
with Company X, finish your pen test with an exfil and see whether any systems picked up a
trace of your ability to access.
Company X, a technology company publicly traded on the market, is a medium to large sized company with approximately 10,000 employees.
The target will be data held internally, such as trade secrets on new technology development (research and development) that may be awaiting patents, sales data, or marketing information that has yet to be released to the public. You know the name of the company, and you want to launch a pen test to see whether you can find where this data may be located and/or saved. Here are the steps (and remember to document what you do and what you find as you go):
1. Find out where the data is stored.
For the example of Company X, you'd do some preemptive reconnaissance work. You discover that the corporate data center and its mirror are in Colorado and Texas.
2. With location information in hand, track down the phone numbers at the main site and start probing from spoofed phone numbers.
You can simply call the help desk and claim to be an internal resource looking to open a ticket and gain helpful information, such as source IPs (so you can get an actual IP address range for the internal network) and some other target information.
3. To gain access externally, use the WhoIs database for DNS and locate a public IP address that you may be able to scan.
The following image shows an example of looking up public information to gain some valuable insight when trying to find an attack vector. Here, if you run a search on a domain, you may be able to find their name servers that may be located on their network. Not all companies do this, but this might provide a clue.
4. Run a ping to get the IP address from the domain name.
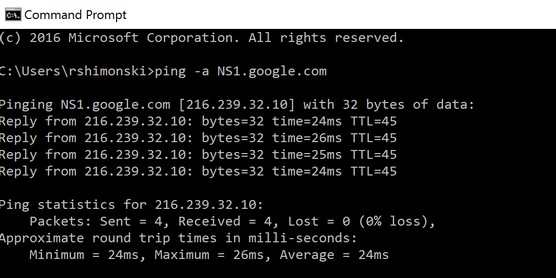
Pinging at a command prompt to get an IP address or range to scan.
5. Start to run Nmap or another tool against that IP.
The goal is to find a public IP address or range to scan with your network mapper, such as Kali or Nmap, which can help to give you some access into the network.
6. Once in, find a way to access your targets.
The target in this case is internally held data. Some of the easiest and most common ways to get the data are these:
• Deploy a piece of malware into the network via email or other means. When users click it, you can gain access to their machine via a Trojan horse and from there you can control it like a zombie to do more reconnaissance work.
• Brute-force attack a router (as an example) on the edge of a network you're scanning to see whether you can gain access by password cracking. In this scenario, say a router is left with HTTP configured and you can probe it with Kali's xhydra, shown below. Using this tool, you can find the router's username and password and can now enter and gain access.
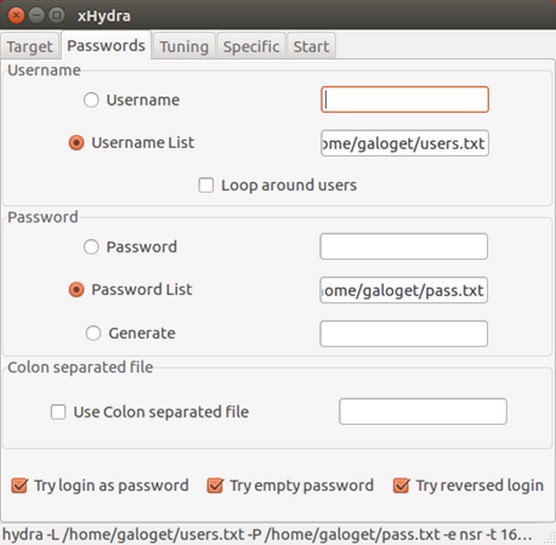
Using Kali (Xhydra) to crack a router password.
7. Once access is gained, get console access and then telnet or SSH to the device.
The goal here is to use the device as a springboard into the next target that you identify.
8. When you have console access, look at the routing table, ARP table, configuration, and other items to develop a manual map of what can be seen.
9. Start to scan, map, and identify the rest of the network looking for assets.
In the following image, a manual map has been created to reflect the pen tester's expectations from this first router hop.
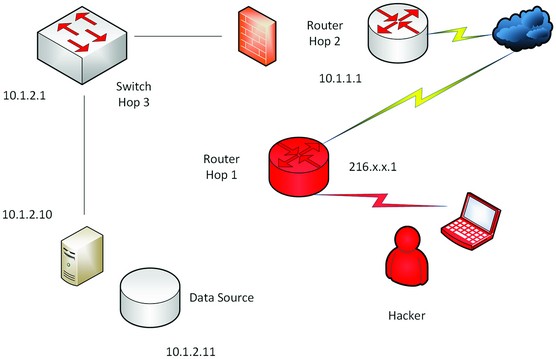
A network map with IP addressing.
10. Begin an APT, a long-term engagement.
At this point in the test, you have done enough to begin an APT — you can lay dormant inside the network and remain undetected for the purpose of continuing research and removing more information.
From moving from one device to another a Unix server has been found (which looks like a dual node cluster) at 10.1.2.10 and 10.1.2.11. Here the pen tester has probed ports and found a possible database port open that I may be able to gain access to.
11. Get out.
You have successfully gained access using tools from basic identification of a possible entry point, built a map, and found a potential database that you can continue to manipulate to get more (hopefully valuable) data.
At this point, you have proved enough that this pen test was successful and can disconnect from the system or get out by shutting down the tool or connection to the system.
Next steps to take after your penetration test
Although it may look like this hack took about five minutes to do, it can take much longer than that. It may take a week to get valuable information that allows you to probe a perimeter network with a public IP address. It may take days to crack a router if it is even set up to answer to non-specified IPs it doesn't know. It can take a long time to get to the next hop, which you may not be able to reach as well.
After you get through these edge devices, you may have a firewall that tracks your movement or flags you as a threat. Host intrusion detection system (IDS) applications such as Tripwire may flag your probes of a critical database system that required priority protection.
This attack may take a long time (for many reasons) for anyone to perform when coming from the outside in. Many hacks come from the inside because, when there is an avenue inside to take, it reduces time and effort just in gaining access. Can it be done? Absolutely, and that is why you do vulnerability assessments and pen tests to find and close every single one of the holes you identified.
What would detection look like if you are caught in the system mimicking a hacker? Well, because you're performing a test, you would likely have given notice that you would be in the system. However, if running a test undetected, you stand the same chance any hacker would in being caught in a system and either terminated (your connection) or left alone based on the protocols of the incident response team.
About the Book Author
Robert Shimonski is an ethical hacker and a professional IT leader who has led numerous efforts to architect, design, strategize and implement enterprise solutions that must remain secure. Rob has been involved in security and technology operations for over 25 years and has written his books from the trenches of experience.
This is an excerpt from:
Pen Testing is necessary for companies looking to target, test, analyze, and patch the security vulnerabilities from hackers attempting to break into and compromise their organizations data. It takes a person with hacking skills to look for the weaknesses that make an organization susceptible to hacking.
Penetration Testing For Dummies aims to equip IT enthusiasts at various levels with the basic knowledge of pen testing. It is the go-to book for those who have some IT experience but desire more knowledge of how to gather intelligence on a target, learn the steps for mapping out a test, and discover best practices for analyzing, solving, and reporting on vulnerabilities.
• The different phases of a pen test from pre-engagement to completion
• Threat modeling and understanding risk
• When to apply vulnerability management vs penetration testing
• Ways to keep your pen testing skills sharp, relevant, and at the top of the game
Get ready to gather intelligence, discover the steps for mapping out tests, and analyze and report results!
Reader Justin T. Manning says "In the past, I used to have issues with countless desktops and software issues requiring outside assistance and dollars spent. Not only does author Robert Shimonski make understanding penetration testing simple, but now I can use this as a reference to do pen testing or learning of hacking.
Reader Michael Pinelli says "It is an all around great book to get you started into the world of penetration testing."
More Network Security Articles:
• Handling Rogue Access Points
• Overview of IPsec with IKEv1
• What is Cross Site Scripting?
• Elementary Information Security
• Avoid Hacks by Rogue Wireless Devices
• Man in the Middle Attack
• The Basics of Network Security
• Prevent Hacking with Password-Cracking Countermeasures
• Difference Between Network Firewall and Web Application Firewall
• How a Firewall Provides Network Security


