NMAP (Network Mapper) Port Scanner
By Stephen Bucaro
When hackers attempt to gain unauthorized access to a computer or server on the
Internet, one of the first things they do is look for open ports. One method of
searching for open ports is TCP SYN scanning, but this can be tedious.
NMAP is a free and open source port
scanner that hackers can use to automate the process of finding open ports to attack.
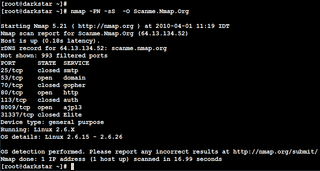
NMAP uses IP packets in a nonstandard way to scan for computers and servers on the
Internet and search for open ports, services available at those ports, and other
information that can be used to hack the system. NMAP is available for the Windows,
Linux, and Mac operating systems.
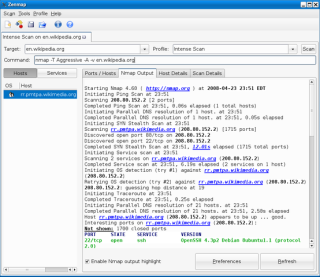
NMAP has a command-line interface but utilities with GUI's are available that work
with NMAP, such as the Zenmap results viewer.
PortSentry
is a Cisco security tool that monitors for both TCP as well as UDP scans and can detect
stealth scans such as those produced by NMAP. PortSentry can be configured to listen on
ports and detect scan attempts and can automatically firewall the scanner's IP address.
NMAP is promoted as a "Security Scanner", and since it's free and open source, it
could indeed be used for security auditing by scanning your own network to see what ports
are available to hackers.
More Network Security Articles:
• How to Use the Open Source Intrusion Detection System SNORT
• NMAP (Network Mapper) Port Scanner
• What is a SQL Injection Attack?
• How a Firewall Provides Network Security
• The Basics of Network Security
• Handling Rogue Access Points
• Designing Physical Network Security
• How Snort's Stealth TCP Port Scanning Works
• How SSL (Secure Sockets Layer) Works
• What is a Botnet Attack and How to Identify It?
| 
