How SSL (Secure Sockets Layer) Works
By Stephen Bucaro
SSL is a security protocol standard that encrypts communication between a web browser and a web server.
Any organization that uses their website to transmit, receive, store, or display confidential or
sensitive information such as passwords, credit card or bank account numbers, social security numbers,
and so on, needs to use an SSL Connection.
To create an SSL secure connection, a digital certificate (also referred to as an "SSL certificate")
is installed on a web server. The digital certificate authenticates the identity of the website, which
guarantees visitors that they're not on a bogus site, and it encrypts the data that's being transmitted.
SSL certificates are issued by Certificate Authorities (CAs), organizations that are trusted to verify
the identity and legitimacy of the entity requesting a certificate. When choosing an SSL provider, keep
in mind that users' web browsers keep a cached list of trusted CAs on file. If a digital certificate is
signed by an entity that's not on the "approved" list, the browser will send a warning message to the
user that the website may not be trustworthy.
There are different types of certificates: a single type secures one domain or one subdomain name,
a wildcard type covers one domain name and an unlimited number of its subdomains, a Multi-Domain
type secures multiple domain names.
Certificates also provide different levels of validation: Domain Validation covers encryption and
verification of the ownership of the domain name registration, Organization Validation in addition
to encryption and verification of ownership of the domain, authenticates other details of the owner like
name and address, Extended Validation (EV) In addition to ownership of the domain and entity
authentication, the legal, physical and operational existence of the entity is verified. EV provides
the highest level of security.
Visitors will know your website has an SSL certificate by the padlock icon to the left of the URL and the
https URL prefix instead of http.
Simplfied SSL Handshake
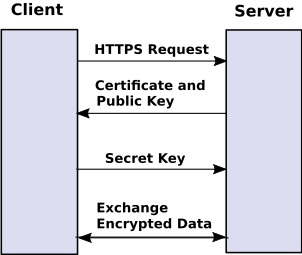
1. client requests HTTPS.
2. Server sends client its certificate and its public key.
3. Client sends server a secret key encrypted with servers public key.
(once a message is encrypted with a public key, only the public key owner's private key can decrypt it.)
4. Client and server can now exchange data encrypted with the shared secret key.
Note: This is a highly simplified explanation of the SSL handshake, in reality during the handshake both
the client and server negotiate which cipher suite to use, and the secret key is actually derived from
random numbers that the client and server exchange, and to minimize the amount of data that can be
stolen or altered if the secret key is cracked, the secret key is usually renegotiated periodically.
After the secret key has been renegotiated, the previous secret key no longer works to decrypt data
encrypted with the new secret key.
More Network Security Articles:
• How to Protect Your Business From a Cyber Attack
• Cyber Security Tips for Small and Medium Business (SMB)
• Security Issues with Wireless LANs
• Nessus Network Vulnerability Scanner
• Remote Access Authentication Protocols
• Firewall Internet Security - The Basics of a Firewall
• Detecting Network Sniffers
• How to Stop Hackers from Invading Your Network
• Network Security Model - Defining an Enterprise Security Strategy
• Email Security
| 
