Man in the Middle Attack
By Stephen Bucaro
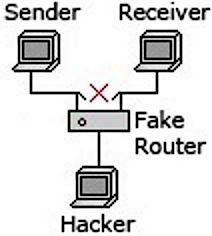
In a Man in the Middle (MIM) attack the hacker places eavesdropping equipment
between the sending device and the receiving device. He intercepts the data,
records it and possibly modifies it, then sends it on to the intended receiving
device. The attack is especially successful if neither the sender nor the receiver
are aware that their data has been compromised.
In a MIM attack the attacker might insert a fake router into the communication
media. The fake router routes packets from the sender's IP address to his
eavesdropping equipment. He then records the data and possibly modifies it.
Then he routes the packets back to the communication media, making sure the
"hop" caused by his fake router is not recorded and the source in the packets is
the original senders IP address. The sender and receiver have no knowledge that
their data has been intercepted.
The defense against MIM attacks is to use strong data encryption. Strong data
encryption requires that the encryption key be verified by a trusted third party
called a Certificate Authority (CA).
More Network Security Articles:
• Digital Signatures and Certificates
• Difference Between Network Firewall and Web Application Firewall
• Denial of Service Attack (DoS) Detection and Mitigation
• Difference Between Rule and Role Based Access Control
• What is Cross Site Scripting?
• Firewall Perimeter Network (DMZ)
• What Roles Do Firewalls and Proxy Servers Play in Network Security?
• What is a Password Hash and Salt?
• Handling Rogue Access Points
• Understanding the Dangers Your Systems Face
| 
