Kerberos Authentication Protocol
By Stephen Bucaro
Kerberos is an authentication protocol developed by MIT (Massachusetts Institute
of Technology), which allows computers communicating over a non-secure network to
prove their identity to one another. It uses the symmetric Needham-Schroeder protocol.
Kerberos provides mutual authentication; both the clent and the server verify each
other's identity.
Kerberos is a suite of free software . It uses symmetric key cryptography which
requires a trusted third party, and optionally may use public-key cryptography during
certain phases of authentication. Kerberos uses port 88 by default. Windows 2000
and later use Kerberos as their default authentication method.
Kerberos uses a trusted third party, called a key distribution center (KDC), which
consists of two parts: an Authentication Server (AS) and a Ticket Granting Server (TGS).
It uses "tickets" which serve to prove the identity of users.
The KDC maintains a database of secret keys; client or server on the network shares
a secret key known only to itself and to the KDC. Knowledge of this key serves to
prove an entity's identity. For communication between two computers, the KDC generates
a session key which they can use to secure their interactions.
The security of the protocol relies heavily on participants maintaining loosely
synchronized time and on short-lived assertions of authenticity called Kerberos tickets.
How Kerberos Works
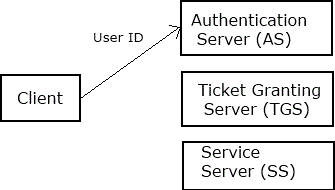
1. The client authenticates itself to the Authentication Server.
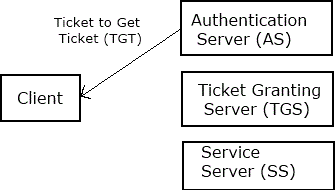
2. The client receives a time-stamped ticket from the Authentication Server.
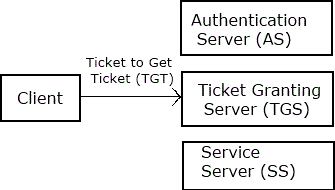
3. The client contacts the Ticket Granting Server (TGS), and using the ticket it demonstrates its identity and asks for a service.
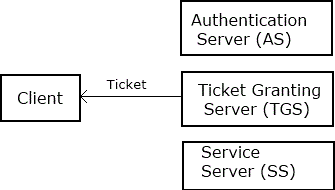
4. If the client is eligible for the service, then the Ticket Granting Server sends another ticket to the client.
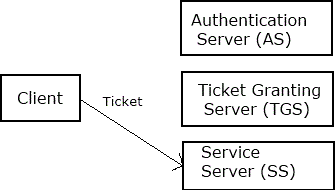
5. The client then contacts the Service Server (SS) , and using this ticket it proves that it has been approved to receive the service.
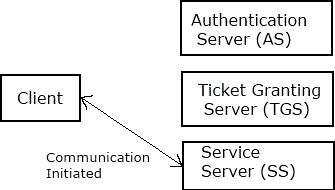
6. Comunication is then initiated between the client and the Service Server.
The client authenticates to the AS once using a long-term shared secret (e.g. a password)
and receives a Ticket to Get Ticket (TGT) from the AS. Later, when the client wants to contact
the same SS, it can (re)use this ticket to get additional tickets from TGS, for SS, without
resorting to using the shared secret. These tickets can be used to prove authentication to SS.
One problem with Kerberos is that it requires continuous availability of a Kerberos server.
When the Kerberos server is down, no one can log in. This can be mitigated by using multiple
Kerberos servers and fallback authentication mechanisms.
Another problem is that Kerberos has strict time requirements, which means the clocks of the
involved hosts must be synchronized. The tickets have a time availability period and if the
host clock is not synchronized with the Kerberos server clock, the authentication will fail.
The default configuration requires that clock times are no more than five minutes apart.
In practice Network Time Protocol daemons are usually used to keep the host clocks synchronized.
More Networking Protocols and Standards:
• IPv6 Flow Label Field
• Shortest Path Bridging (SPB) Protocol
• The OSI Presentation Layer
• Network Cabling and Components
• Video - Transport Layer (Layer 4) of OSI Networking Model
• Neighbor Discovery Protocol (NDP)
• The OSI Reference Model
• Routing Datagrams
• IPv4 to IPv6 Transition With the Dual-Stack Technique
• IP Addressing and Subnetting
| 
