To better understand how malware autostarts in Windows, lets take a quick look at how Windows boots up. Depending on whether the system is BIOS-based or EFI-based, the bootup process differs up to the point of passing control to the Kernel.
BIOS-Based System
On a BIOS-based system, the bootup process begins with the BIOS. The BIOS code selects a boot device and loads that device's Master Boot Record (MBR) into memory. The MBR is 512 bytes in size and is located at the first sector of the device. It contains the boot code and the partition table. The partition table contains the location of the primary partition in the disk. After the MBR is loaded, the BIOS passes control to the MBR boot code.
The boot code parses the partition table and looks for a bootable partition. This is also called the system partition. After it is found, the MBR book code reads the system partition's boot sector, which is found at the system partition's first sector. The MBR then passes control to the boot sector code, which informs Windows on the nature of the volume and loads the Bootmgr file from the volume's root directory, after which, control is passed to the Bootmgr.
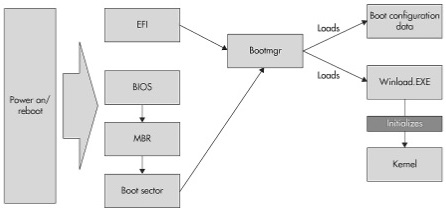
A simplistic view of the bootup process
Bootmgr operates in real mode. This means that what's on disk is what's in memory. There is no virtual-to-physical translation of memory. But the first thing it does is switch the operational mode of the CPU to protected mode. As a result, the full 32 bits of memory become accessible, enabling the Bootmgr to access not just the first 1 MB (20 bits) of physical memory, a limitation in real mode, but all of them. For Windows to operate normally, the system must be running in protected mode with paging enabled. So after switching to protected mode, the Bootmgr also enables paging.
Note
For BIOS-based systems, the Bootmgr briefly switches back to real mode to execute BIOS
functions, especially if Bootmgr needs to access the computer display and integrated
development environment (IDE) disks.
Once the system is running in protected mode with paging enabled, the Bootmgr then loads the Boot Configuration Data (BCD) store in the Boot folder located on the root directory of the system volume. As defined by Microsoft, the BCD store contains boot configuration parameters and controls how the operating system is started in newer versions of Microsoft operating systems, starting with Microsoft Vista and Microsoft Server 2008 operating systems. Once the BCD is loaded, it directs the Bootmgr to the partition where Windows is located. This is also known as the boot partition of the boot volume. From here, the Bootmgr loads Winload.ext, which is Windows' boot loader.
LINGO
As Microsoft puts it, the system partition contains the hardware-related files
that tell a computer where to look to start Windows. A Boot partition is a
partition that contains the Windows operating system files, which are located in the
Windows file folder. Usually, these are the same partition, especially if you have
only one operating system installed on your computer. If you have a multiboot computer,
you will have more than one boot partition.
Note
The BCD can have multiple boot-selection entries that can include other operating systems.
If this is the case, the Bootmgr displays the OS choices to the user and the user decides
which one to boot. If the user does not choose anything within the time limit, Bootmgr
loads the boot loader of the default OS.
Now that control is passed to the Windows OS loader, Winload.exe, it gathers hardware description about the system and then loads the files needed to initialize the kernel. It loadsd Ntoskrnl.exe and Hal.dll and their dependencies. Winload.exe then rerads the SYSTEM registry hive located in \Windows\System32\Config\System. The SYSTEM registry hive contains the boot device drivers that must be loaded to boot the system. The registry path that contains the subkeys of the boot device drivers is HKLM\SYSTEM\CurrentControlSet\Services. It contains not just the subkeys of boot device drivers, but subkeys of all device drivers. To differentiate which is which, Winload.exe identifies boot device drivers through their start value. Boot device drivers have a start value of SERVICE_BOOT_START(0). Once they are identified, Winload.exe loads these drivers and then prepares the CPU registers for Ntoskrnl.exe. It then calls KiSystemStartup, the Ntoskrnl.exe's main function.
EFI-Based System
EFI stands for Extensible Firmware Interface. One of the differences it has over BIOS-based systems is that it does not rely on MBR boot code. The EFI has its own boot manager that can read the partition table to determine which partition is bootable. This means that the boot code itself is in the firmware. Once the EFI's boot manager loads into memory and executes, the succeeding steps are similar to the BIOS-based startup process.
LINGO
A registry hive contains a registry subtree.
This is an excerpt from:
Learn how to improve the security posture of your organization and defend against some of the most pervasive network attacks. Malware, Rootkits & Botnets A Beginner's Guide explains the nature, sophistication, and danger of these risks and offers best practices for thwarting them.
After reviewing the current threat landscape, the book describes the entire threat lifecycle, explaining how cybercriminals create, deploy, and manage the malware, rootkits, and botnets under their control. You'll learn proven techniques for identifying and mitigating these malicious attacks. Templates, checklists, and examples give you the hands-on help you need to get started protecting your network right away.
A reader says, "This book demystifies the complexities of a very critical topic anyone with a computer or device must know. The book takes the reader into a journey of understanding the world of malware, rootkits and botnets. The good part about this journey is that there is no experience required. It is a very easy read and you won't get stumped or trapped in technical jargon. Instead, the book explains these jargons so you can carry a very intelligent conversation about malware with industry experts."
Reader Ricardo A Dionisio says, "Very nice book. Was able to really comprehend the basic of the "new threats" on the digital world. Christopher is very knowledgeable on this field. Will look forward on new books from this author. A++."
For more information click here
More Windows Administration Information:
• Botnets - What Are They?
• Avoid the Indigestion of Cookies
• Phishing Attacks
• Computer Architecture, Hardware domain of the CISSP Exam
• Five Things You Can Do To Improve Your Company's Security
• Video - Protect Your Files with Free SafeHouseExplorer Encryption Application
• Disable Remote Access
• Computer Architecture, Main Memory, and the CISSP Exam
• Firefox Security Options
• Top Eleven Tips for Safe Computing



