Routing Datagrams
Internet gateways are commonly (and perhaps more accurately) referred to as IP routers
because they use Internet Protocol to route packets between networks. In traditional
TCP/IP jargon, there are only two types of network devices - gateways and hosts.
Gateways forward packets between networks, and hosts don't. However, if a host is
connected to more than one network (called a multi-homed host), it can forward
packets between the networks. When a multi-homed host forwards packets, it acts just
like any other gateway and is in fact considered to be a gateway. Current data communications
terminology makes a distinction between gateways and routers, but we'll use the terms
gateway and IP router interchangeably.
Figure 1-6 shows the use of gateways to forward packets. The hosts (or end systems)
process packets through all four protocol layers, while gateways (or intermediate
systems) process the packets only up to the Internet Layer where the routing decisions are made.
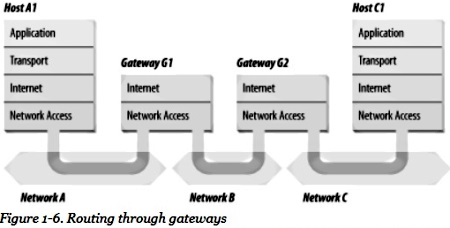
Systems can deliver packets only to other devices attached to the same physical
network. Packets from A1 destined for host C1 are forwarded though gateways G1 and G2.
Host A1 first delivers the packet to gateway G1, with which it shares network A.
Gateway G1 delivers the packet to G2 over network B. Gateway G2 then delivers the
packet directly to host C1 because they are both attached to network C. Host A1 has
no knowledge of any gateways beyond gateway G1. It sends packets destined for both
networks C and B to that local gateway and then relies on that gateway to properly
forward the packets along the path to their destinations. Likewise, host C1 sends its
packets to G2 to reach a host on network A, as well as any host on network B.
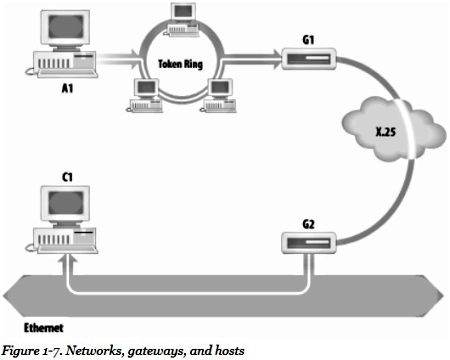
Figure 1-7 shows another view of routing. This figure emphasizes that the underlying
physical networks a datagram travels through may be different and even incompatible.
Host A1 on the token ring network routes the datagram through gateway G1 to reach
host C1 on the Ethernet. Gateway G1 forwards the data through the X.25 network to
gateway G2 for delivery to C1. The datagram traverses three physically different
networks, but eventually arrives intact at C1.
The above is an excerpt from: TCP/IP Network Administration (3rd Edition; O'Reilly Networking)



Reader G. Maxwell says,"As with all of O'Reilly's books, this one is technically accurate and fundamentally sound.
It does not teach TCP/IP from a simplistic approach - telling you only what you need to know and leaving you begging
for more. It lays a ground work based upon the actual theory of these protocols and how they were developed and the
thinking that was involved in their creation. From there, it takes you step by step through the layers of the
protocols and presents everything that most people would need to know--even more than they would need to know.
Especially enlightening were the chapters on IPv6 - the next generation of the IP protocol, and the chapter covering
subnetting. Overall, if you need the one book to explain TCP/IP and the "ins-and-outs" of these networking protocols,
look no further. This book has all you'll need.
More Networking Protocols and Standards:
• The OSI Physical Layer
• Free eBook: Introduction to 802.11 Wireless
• Network Routing Protocols - IGRP, EIGRP, OSPF, ISIS, BGP
• IEEE 802.11 Wireless Modulation Methods
• Internet Protocol versions IPv4, IPv5 and IPv6
• Networking Routing Believability and Administrative Distance
• IPv6 Anycast Addresses
• IPv6 Payload Length Field and Jumbograms
• Ports and Sockets
• Video - Data Link Layer of OSI Networking Model
| 
