When you use a shared PC, if you don't want to leave any evidence of your browsing or search history for others to see, you can set InPrivate Browsing. InPrivate Browsing is a feature of Internet Explorer 9 that prevents your browsing history, temporary Internet files, form data, cookies, and user names and passwords from being retained by the browser.
When using InPrivate Browsing
1. Sites you visited will not be added to the list of sites in the history menu.
2. Files you download will not be listed in the Download window.
3. No user names or passwords will be saved.
4. Text you type in the Search bar and forms will not be saved for auto-complete.
5. Cookies will not be stored.
6. No temporary internet or cached files will be saved.
To enter InPrivate Browsing, in Internet Explorer's main menu select Tools | InPrivate Browsing.
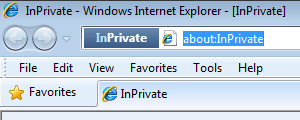
Internet Explorer will launch a new browser session that won’t keep any information about webpages you visit or searches you perform. Note the InPrivate indicator in the address bar. Any new windows launched from the InPrivate session will also be InPrivate.
Closing the InPrivate browser window will end your InPrivate browsing session, so next time you open the browser, and want to do private browsing, you need to re-select it in the menu.
More Windows Administration Information:
• What Are WEP, WPA, TKIP, AES and PSK?
• Fundamentals of Windows Security
• Don't Let a Ransomware Attack Hold Your Data Hostage
• Disable Remote Access
• How Many Spyware Items Are Slowing Down Your Computer?
• Remove Spyware with Spybot - Search & Destroy
• What's a Root Kit and How Hackers Are Getting Into Your Computer With It
• Computer Architecture, Software and Firmware, and the CISSP Exam
• Computer Technician's Guide to Biometric Security Devices
• Set Windows 10 Controlled Folder Access to Protect Against Ransomware

