Using abstraction to split computing systems into components makes things easier to understand, but it doesn't work without organization. We arrange components into layers or levels. A layer or level is a classification (or grouping) of a component according to where that component sits between the user and the hardware. Web browsers, games, and such sit at the top layer; at the bottom layer we have the memory in the computer hardware - the 0s and 1s. The operating system occupies most of the layers in between.
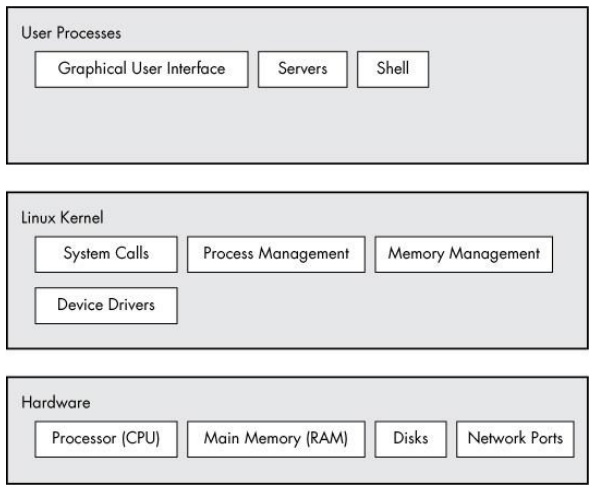
Figure 1-1. General Linux system organization
A Linux system has three main levels. Figure 1-1 shows these levels and some of the components inside each level. The hardware is at the base. Hardware includes the memory as well as one or more central processing units (CPUs) to perform computation and to read from and write to memory. Devices such as disks and network interfaces are also part of the hardware.
The next level up is the kernel, which is the core of the operating system. The kernel is software residing in memory that tells the CPU what to do. The kernel manages the hardware and acts primarily as an interface between the hardware and any running program.
Processes - the running programs that the kernel manages - collectively make up the system's upper level, called user space. (A more specific term for process is user process, regardless of whether a user directly interacts with the process. For example, all web servers run as user processes.)
There is a critical difference between the ways that the kernel and user processes run: The kernel runs in kernel mode, and the user processes run in user mode. Code running in kernel mode has unrestricted access to the processor and main memory. This is a powerful but dangerous privilege that allows a kernel process to easily crash the entire system. The area that only the kernel can access is called kernel space.
User mode, in comparison, restricts access to a (usually quite small) subset of memory and safe CPU operations. User space refers to the parts of main memory that the user processes can access. If a process makes a mistake and crashes, the consequences are limited and can be cleaned up by the kernel. This means that if your web browser crashes, it probably won't take down the scientific computation that you've been running in the background for days.
In theory, a user process gone haywire can't cause serious damage to the rest of the system. In reality, it depends on what you consider "serious damage," as well as the particular privileges of the process, because some processes are allowed to do more than others. For example, can a user process completely wreck the data on a disk? With the correct permissions, yes - and you may consider this to be fairly dangerous. There are safeguards to prevent this, however, and most processes simply aren't allowed to wreak havoc in this manner.
About the Author
Brian Ward has been working with Linux since 1993. He is the author of The Linux Kernel-HOWTO, The Book of VMware, and The Linux Problem Solver.

Unlike some operating systems, Linux doesn't try to hide the important bits from you - it gives you full control of your computer. But to truly master Linux, you need to understand its internals, like how the system boots, how networking works, and what the kernel actually does.
In this third edition of the bestselling How Linux Works, author Brian Ward peels back the layers of this well-loved operating system to make Linux internals accessible. This edition has been thoroughly updated and expanded with added coverage of Logical Volume Manager (LVM), virtualization, and containers.
You'll learn:
• How Linux boots, from boot loaders to init (systemd)
• How the kernel manages devices, device drivers, and processes
• How networking, interfaces, firewalls, and servers work
• How development tools work and relate to shared libraries
• How to write effective shell scripts
You'll also explore the kernel and examine key system tasks inside user-space processes, including system calls, input and output, and filesystem maintenance. With its combination of background, theory, real-world examples, and thorough explanations, How Linux Works, 3rd Edition will teach you what you need to know to take control of your operating system.
New to This Edition:
• Hands-on coverage of the LVM, journald logging system, and IPv6
• Additional chapter on virtualization, featuring containers and cgroups
• Expanded discussion of systemd
Reader Garret P. Arcoraci says, "I teach System Administration at the Rochester Institute of Technology; usually, I don't make a book a requirement, but this is the exception. Highly recommend it to anyone looking for a deeper understanding of the Linux operating system and traditional computer architecture."
More Windows Administration Information:
• Fedora 3 Modem Installation
• Check Used Disk Space on Linux With du Command
• Welcome to the world of Knoppix
• Connecting Linux to the Internet
• Linux System Calls and Support
• Linux Process Management
• What is Bash?
• Easy Way to Install Linux
• Linux Installation CDs vs. Linux "Live" CDs
• How to install software applications on Linux


