The kernel runs processes in kernel mode, and the user processes run in user mode. Code running in kernel mode has unrestricted access to the processor and main memory. User mode, in comparison, restricts access to a (usually quite small) subset of memory and safe CPU operations.
There are several kinds of kernel features available to user processes. For example, system calls (or syscalls) perform specific tasks that a user process alone cannot do well or at all. For example, the acts of opening, reading, and writing files all involve system calls.
Two system calls, fork() and exec(), are important to understanding how processes start up:
• fork() When a process calls fork(), the kernel creates a nearly identical copy of the process.
• exec() When a process calls exec(program), the kernel starts program, replacing the current process.
Other than init, all user processes on a Linux system start as a result of fork(), and most of the time, you also run exec() to start a new program instead of running a copy of an existing process. A very simple example is any program that you run at the command line, such as the ls command to show the contents of a directory. When you enter ls into a terminal window, the shell that’s running inside the terminal window calls fork() to create a copy of the shell, and then the new copy of the shell calls exec(ls) to run ls. Figure 1-2 shows the flow of processes and system calls for starting a program like ls.
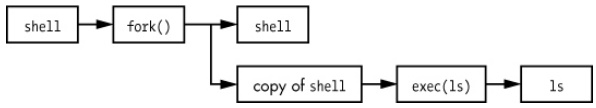
Figure 1-2. Starting a new process
NOTE: System calls are normally denoted with parentheses. In the example shown in Figure 1-2, the process asking the kernel to create another process must perform a fork() system call. This notation derives from the way the call would be written in the C programming language. You don’t need to know C to understand this book; just remember that a system call is an interaction between a process and the kernel. In addition, this book simplifies certain groups of system calls. For example, exec() refers to an entire family of system calls that all perform a similar task but differ in programming.
The kernel also supports user processes with features other than traditional system calls, the most common of which are pseudodevices. Pseudo-devices look like devices to user processes, but they’re implemented purely in software. As such, they don’t technically need to be in the kernel, but they are usually there for practical reasons. For example, the kernel random number generator device (/dev/random) would be difficult to implement securely with a user process.
NOTE: Technically, a user process that accesses a pseudodevice still has to use a system call to open the device, so processes can’t entirely avoid system calls.
About the Author
Brian Ward has been working with Linux since 1993. He is the author of The Linux Kernel-HOWTO, The Book of VMware, and The Linux Problem Solver.
Unlike some operating systems, Linux doesn't try to hide the important bits from you - it gives you full control of your computer. But to truly master Linux, you need to understand its internals, like how the system boots, how networking works, and what the kernel actually does.
In this third edition of the bestselling How Linux Works, author Brian Ward peels back the layers of this well-loved operating system to make Linux internals accessible. This edition has been thoroughly updated and expanded with added coverage of Logical Volume Manager (LVM), virtualization, and containers.
You'll learn:
• How Linux boots, from boot loaders to init (systemd)
• How the kernel manages devices, device drivers, and processes
• How networking, interfaces, firewalls, and servers work
• How development tools work and relate to shared libraries
• How to write effective shell scripts
You'll also explore the kernel and examine key system tasks inside user-space processes, including system calls, input and output, and filesystem maintenance. With its combination of background, theory, real-world examples, and thorough explanations, How Linux Works, 3rd Edition will teach you what you need to know to take control of your operating system.
New to This Edition:
• Hands-on coverage of the LVM, journald logging system, and IPv6
• Additional chapter on virtualization, featuring containers and cgroups
• Expanded discussion of systemd
Reader Garret P. Arcoraci says, "I teach System Administration at the Rochester Institute of Technology; usually, I don't make a book a requirement, but this is the exception. Highly recommend it to anyone looking for a deeper understanding of the Linux operating system and traditional computer architecture."
More Windows Administration Information:
• Commands to Display Your Linux Computer's Hardware Information
• The Fedora 3 Linux File Structure
• What Is the Android Operating System?
• Migrating to Linux: Installing Software
• Bootloaders In Linux
• Virtual Desktop Infrastructure (VDI) With Ubuntu Linux
• Dual-Boot Windows and Ubuntu
• View Your Linux Server's Network Connections With Netstat
• Fedora 3 Linux File Management
• Installing Fedora 3 Linux



